Set Up User and Group Provisioning
We have some AD Users and AD Groups. We need to set up which ones are synchronized with AWS SSO. Hint: Pretty much all of them.
Assign User and Groups
The AWS Single Sign-On Enterprise Application requires users and groups to be assigned so that they are synchronized.
Find the AWS Single Sign-on Enterprise Application.
Click "Enterprise applications".
Click "AWS Single Sign-on".
Click "Assign users and groups".
Click "Add user/group". The "Users and groups" on the next page.
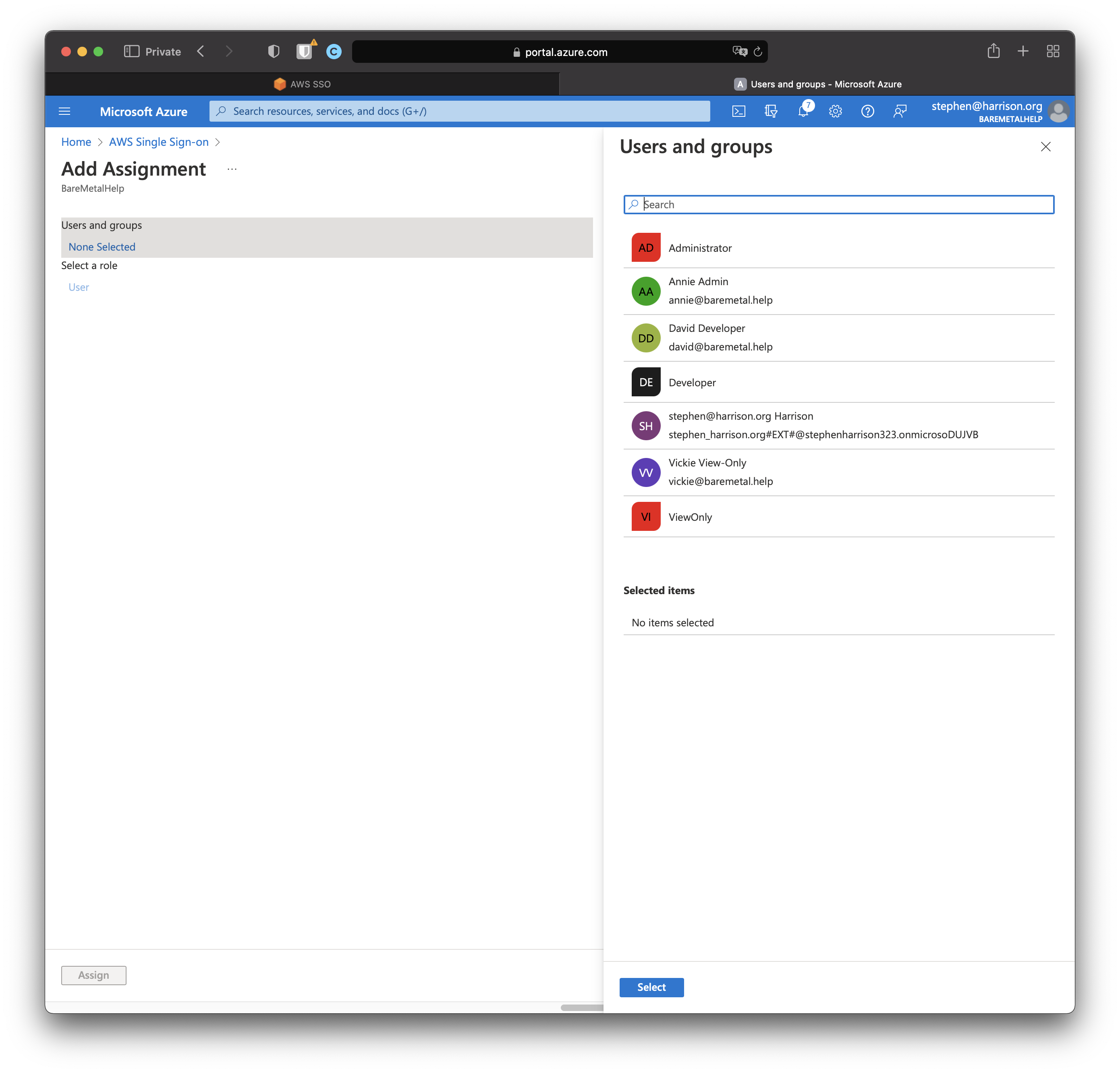
Add all users and groups. I have my user in AD as the owner. It's not at all necessary.
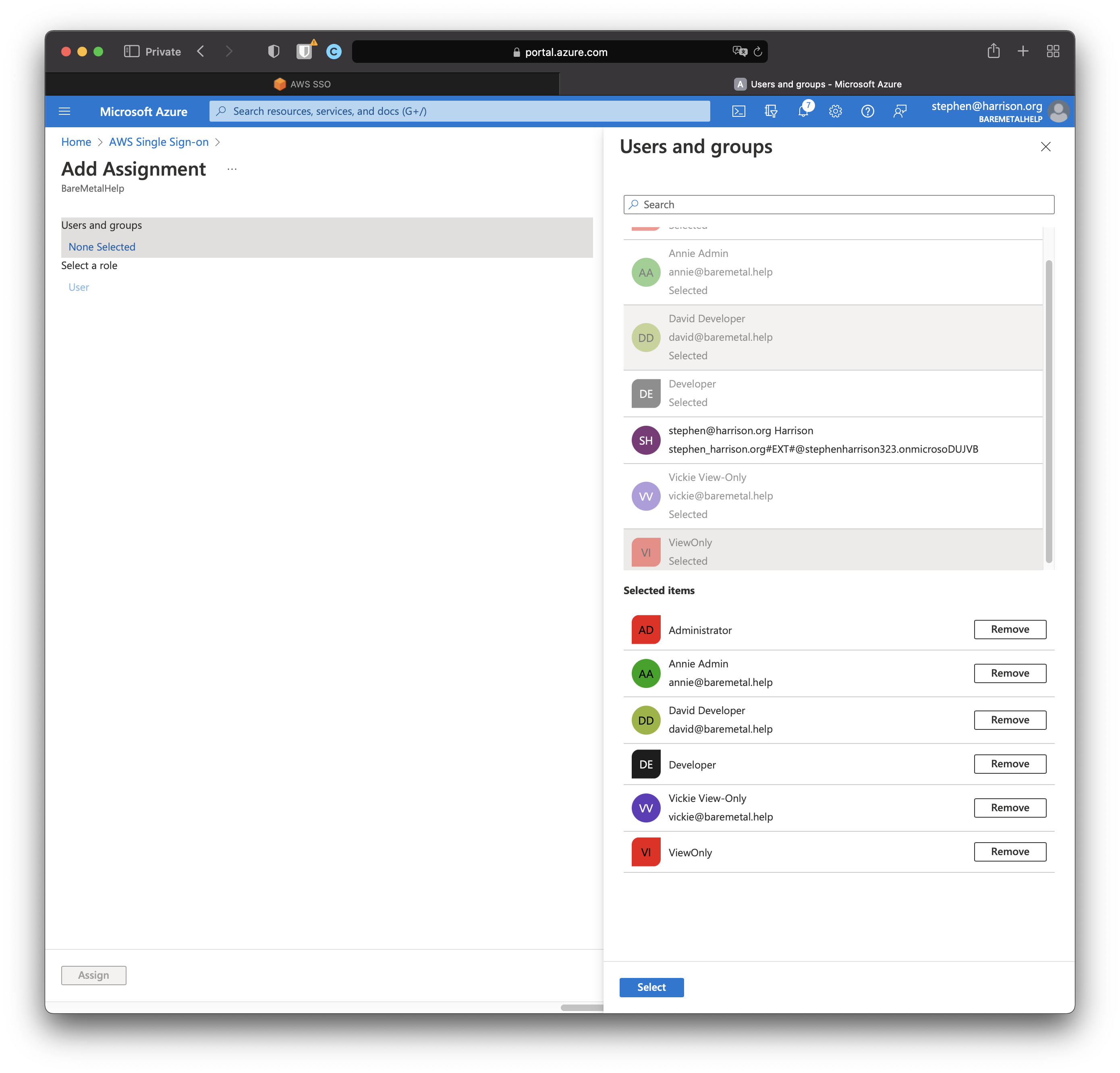
Click "Select" to add all the assignments. Click "Assign" to make it happen.
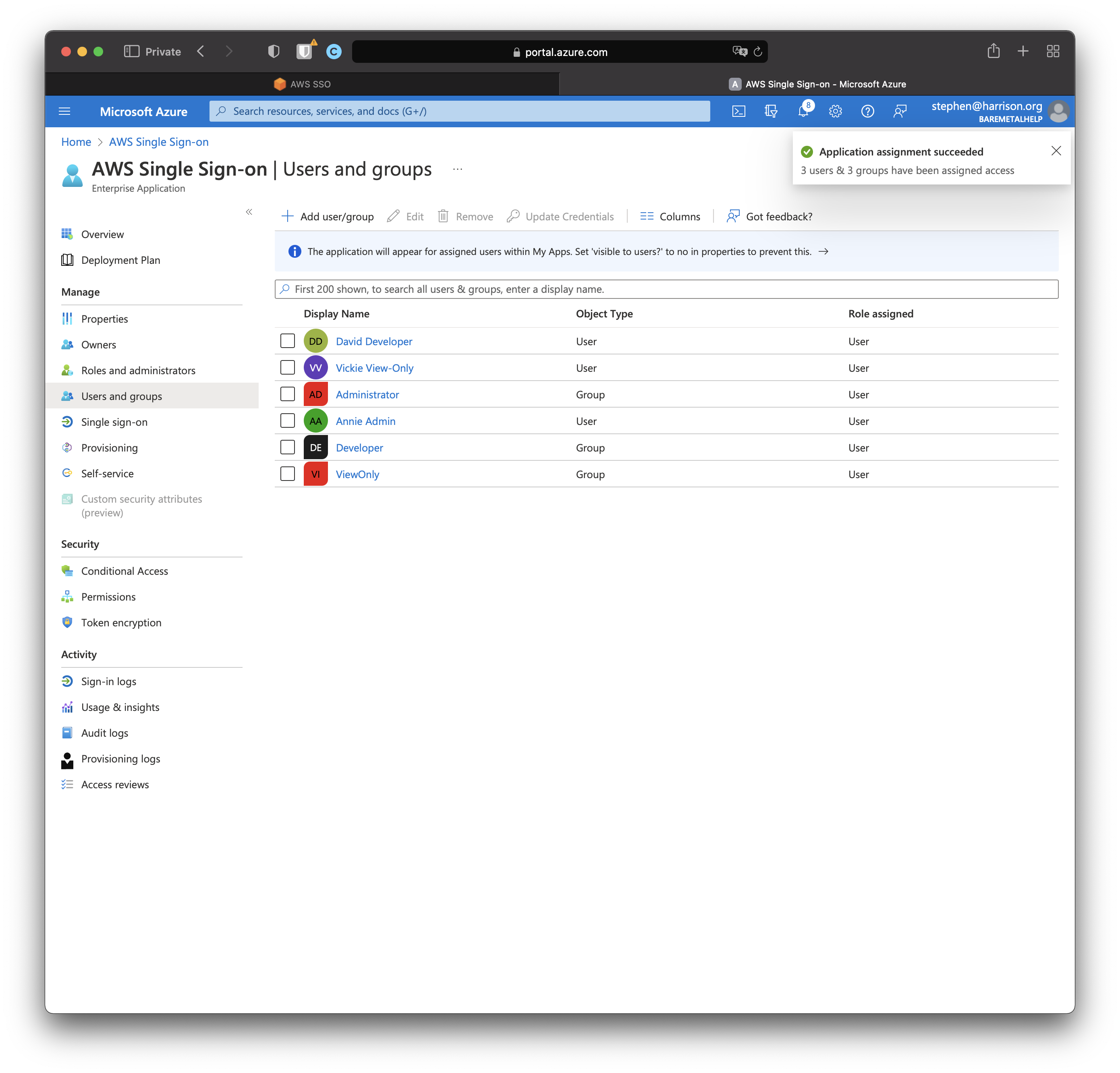
Provision User and Groups for Synchronization
Now that we have assigned which AD User and Groups will be synchronized to AWS SSO Users and Groups, it's time to set up the synchronization job itself.
In the AWS Single Sign-on Enterprise Application, click "Provisioning".
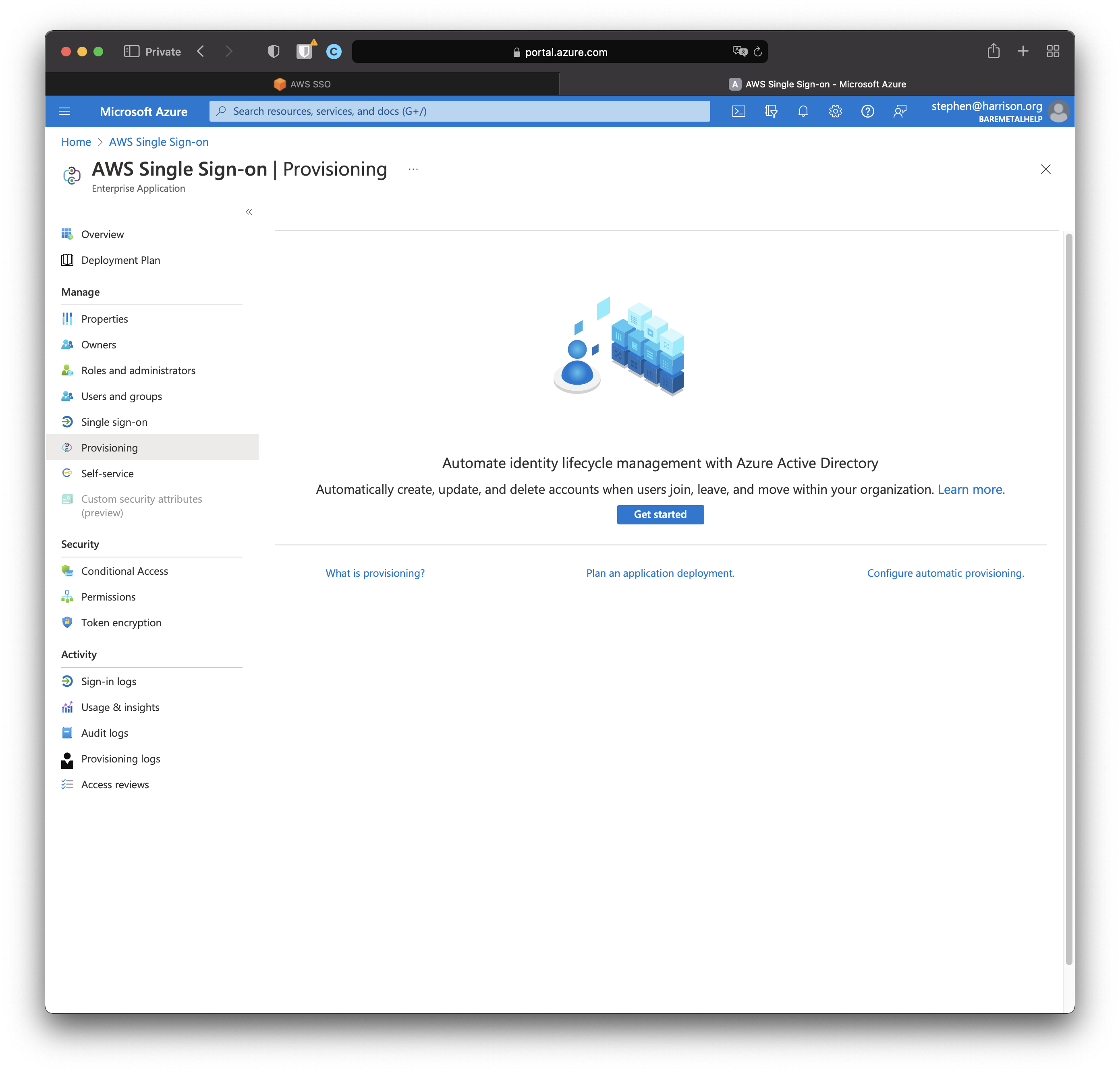
Click "Get started"
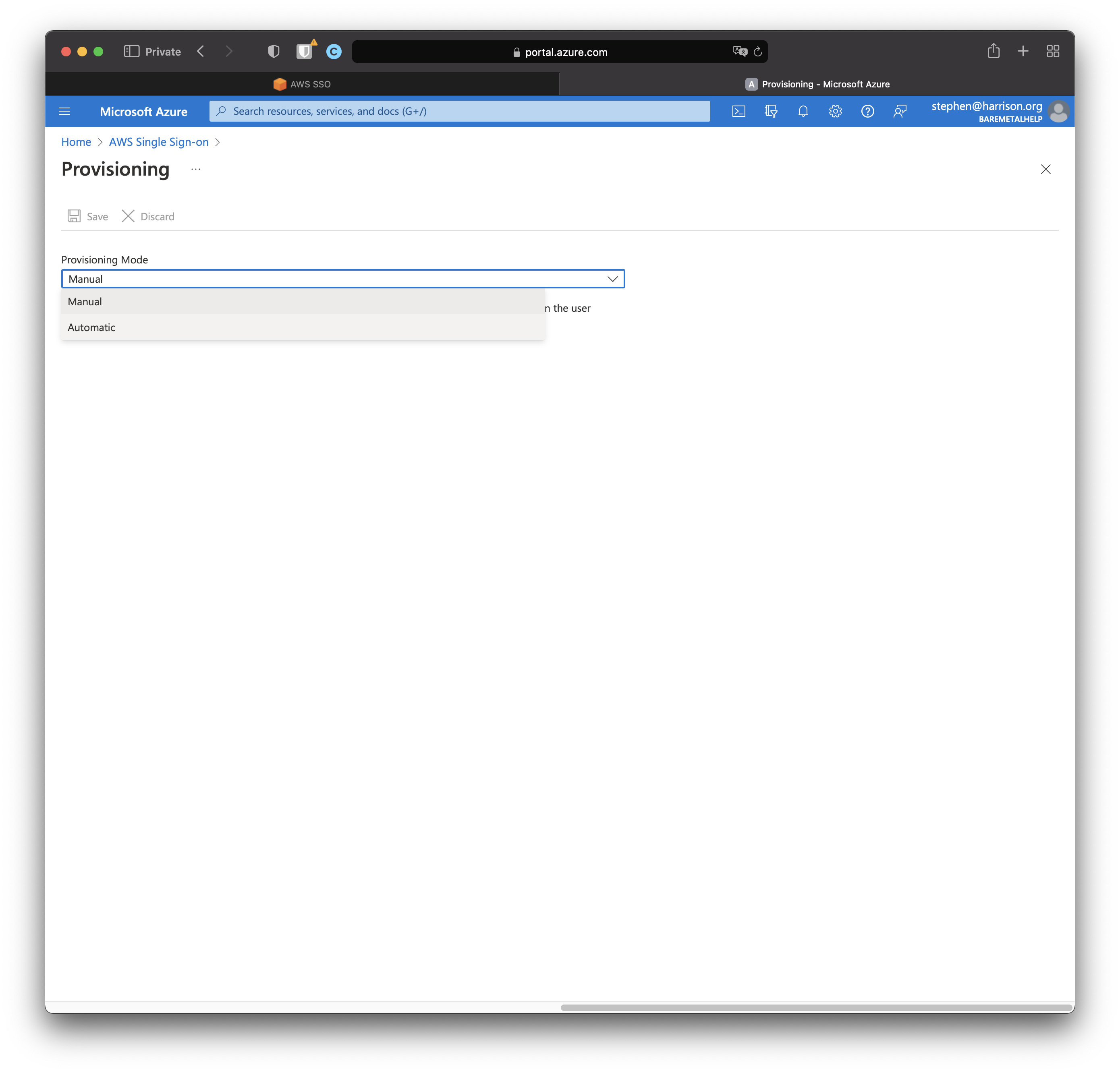
Select "Automatic".
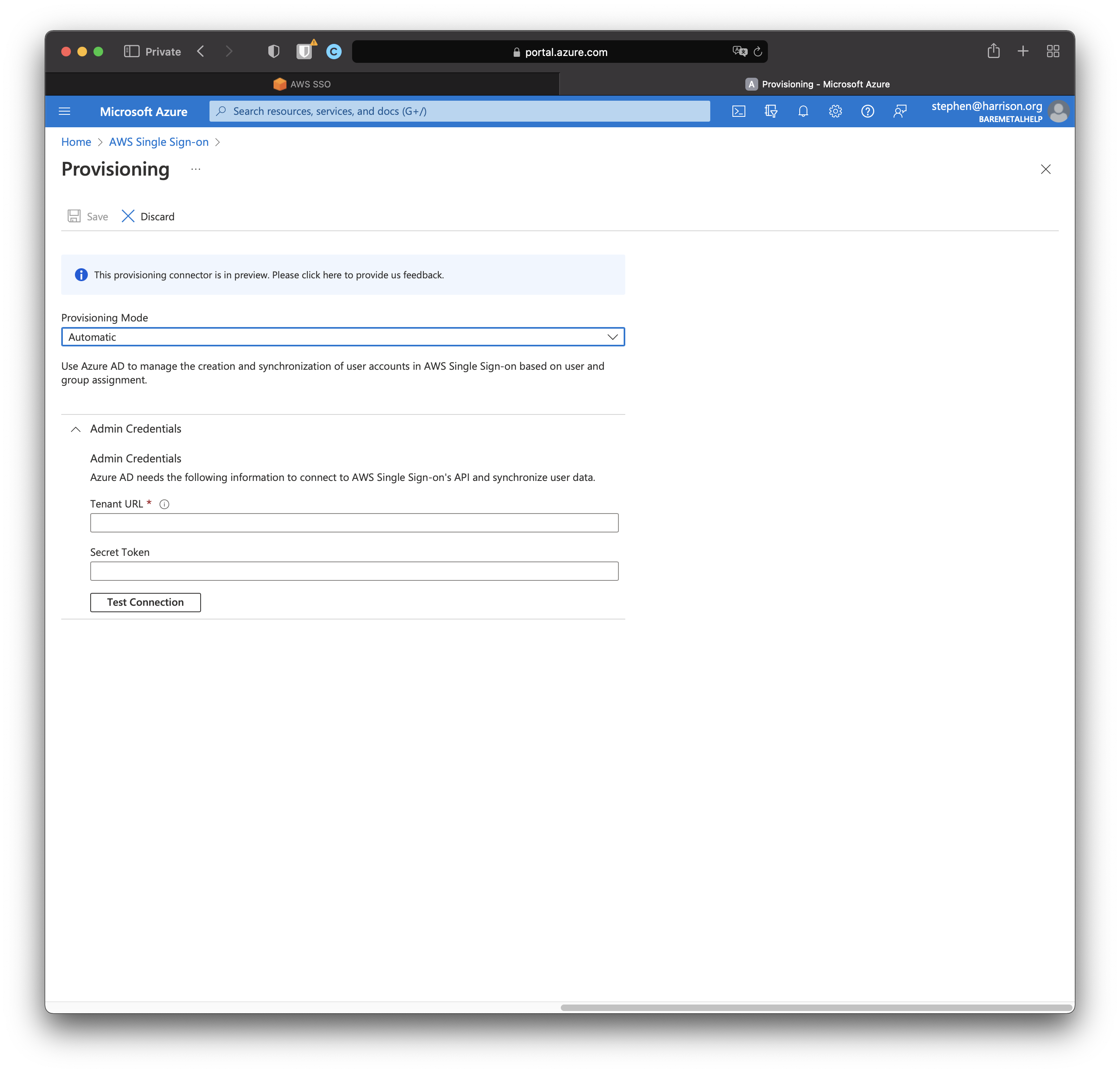
Back to AWS SSO Console
AD automatic provisioning requires a Tenant URL and a Secret Token. We get these from the AWS.
In the AWS SSO Console.
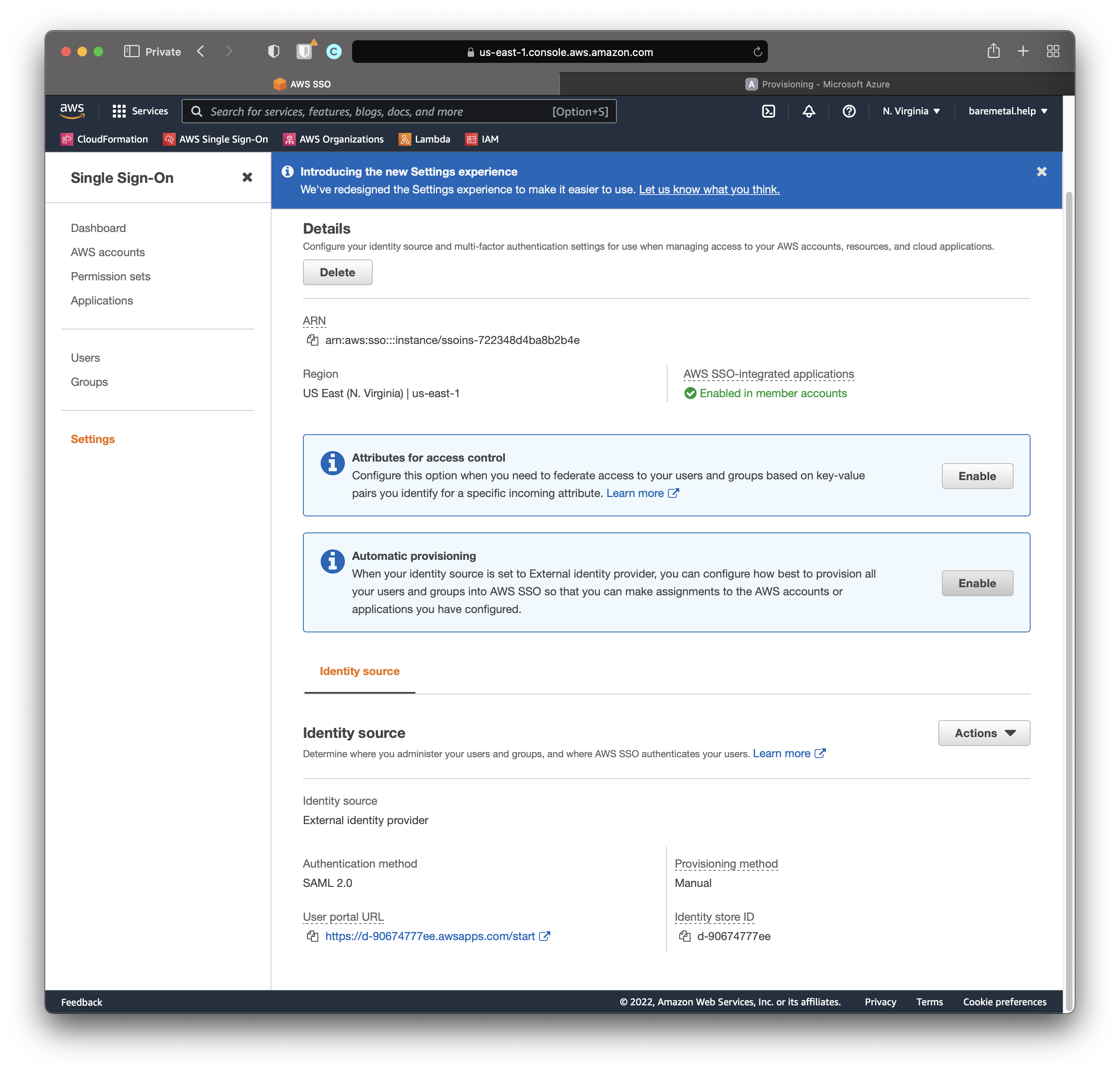
Click "Enable" next to "Automatic Provisioning".
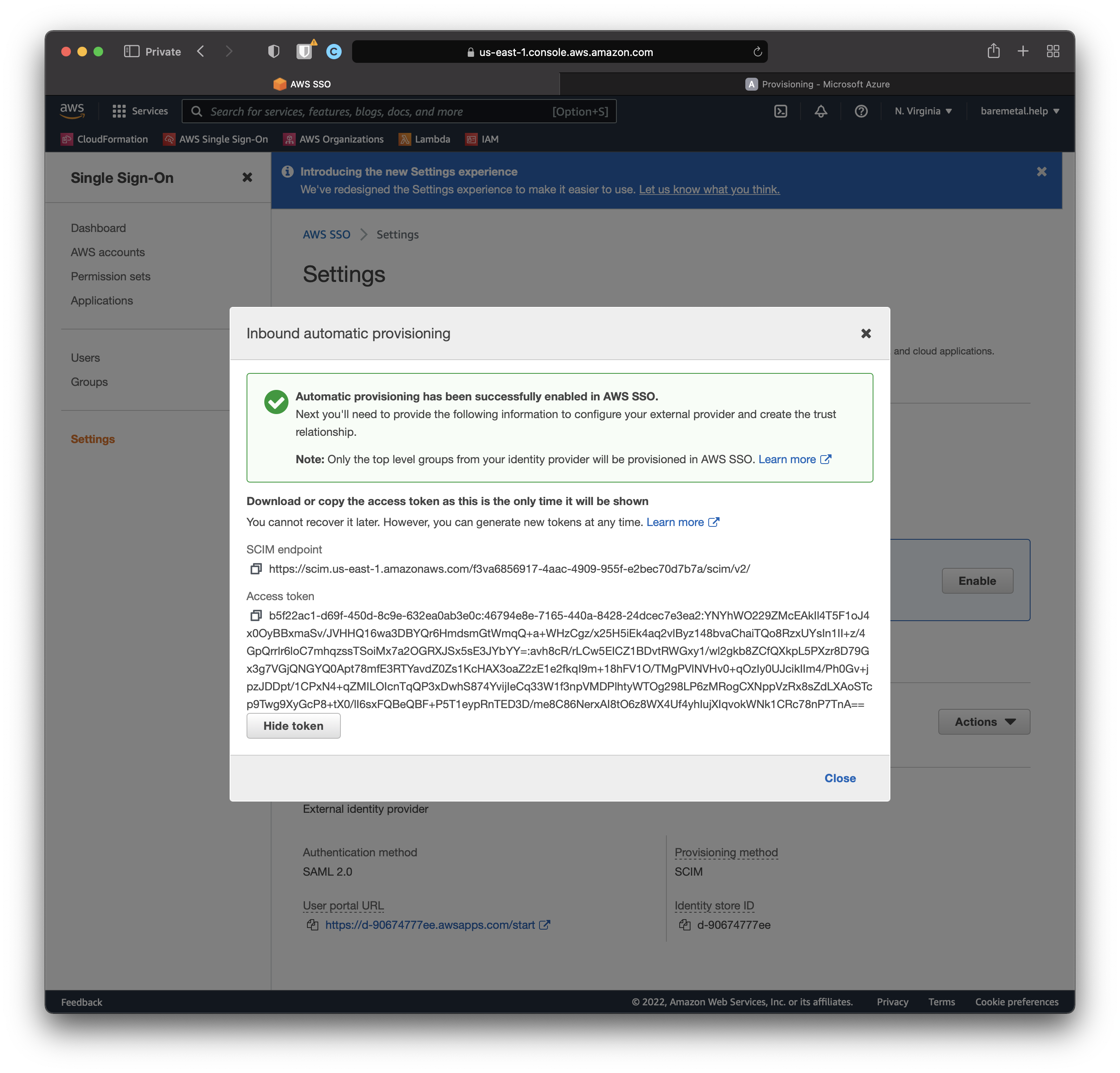
Copy "SCIM endpoint" URL to "Tenant URL" in the AD Provisioning console.
Copy "Access token" to "Secret Token" in the AD Provisioning console.
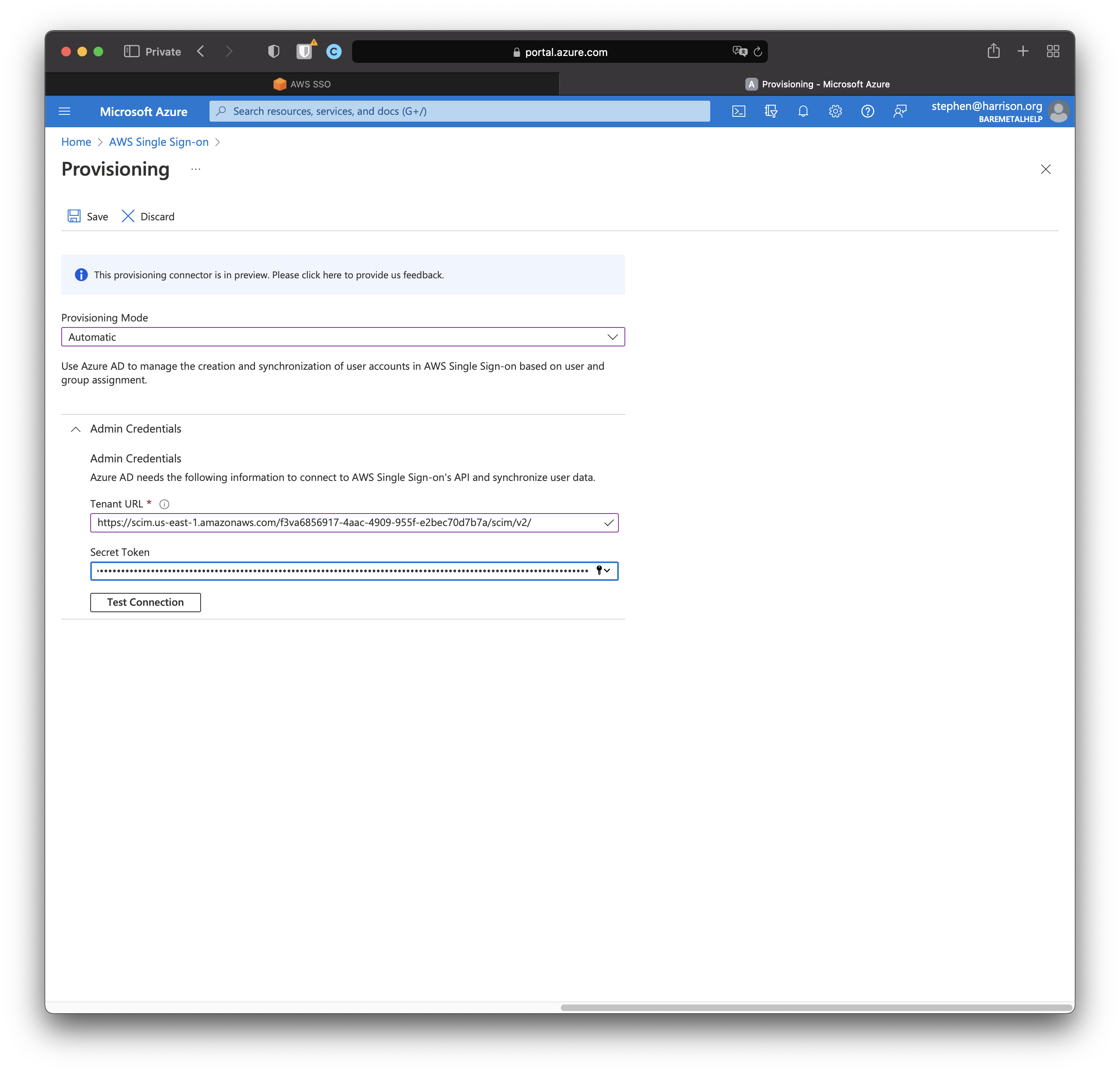
Click "Test Connection".
Here's what success looks like.
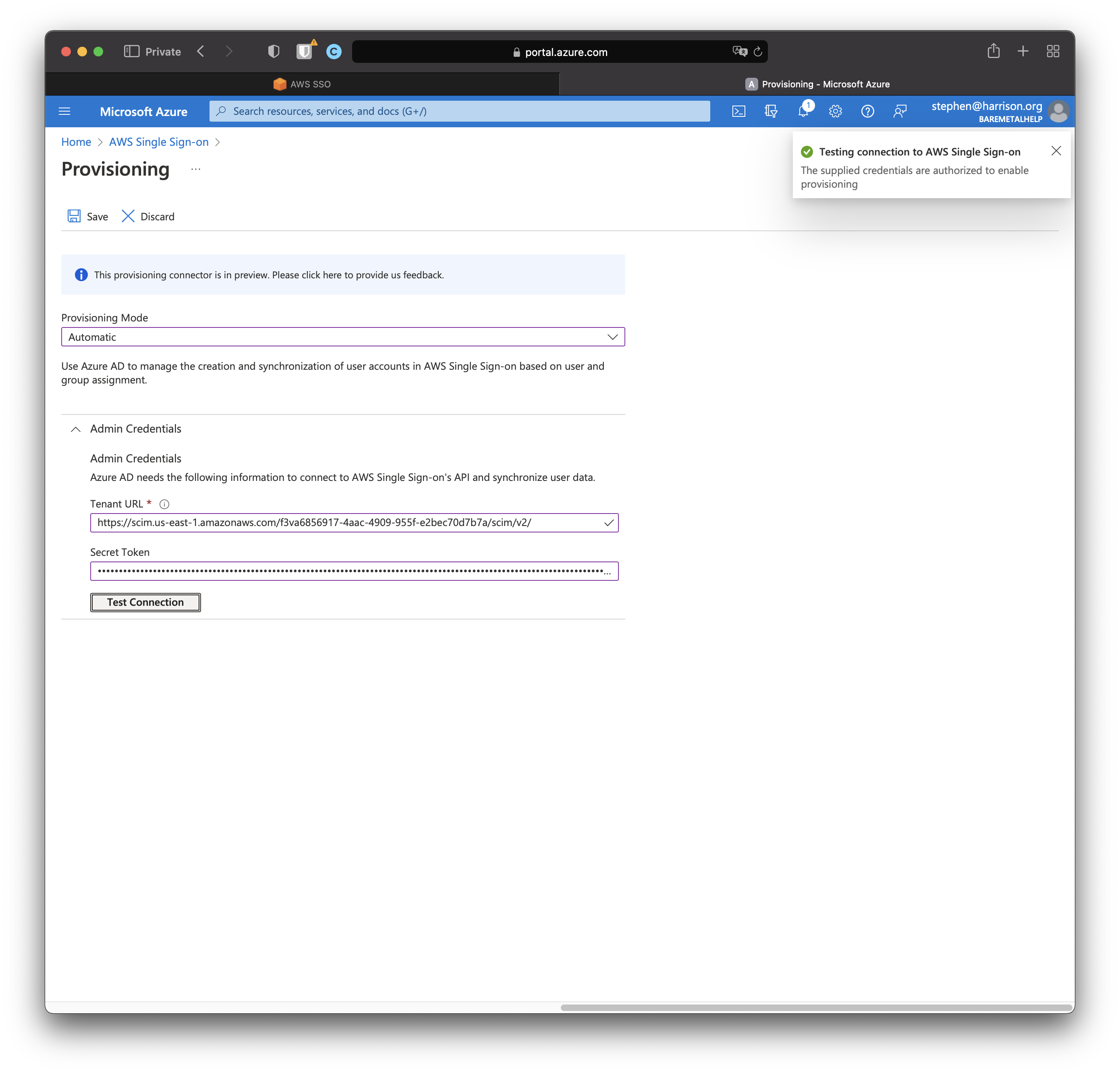
Click "Save".
Here's the initial provisioning configuration.
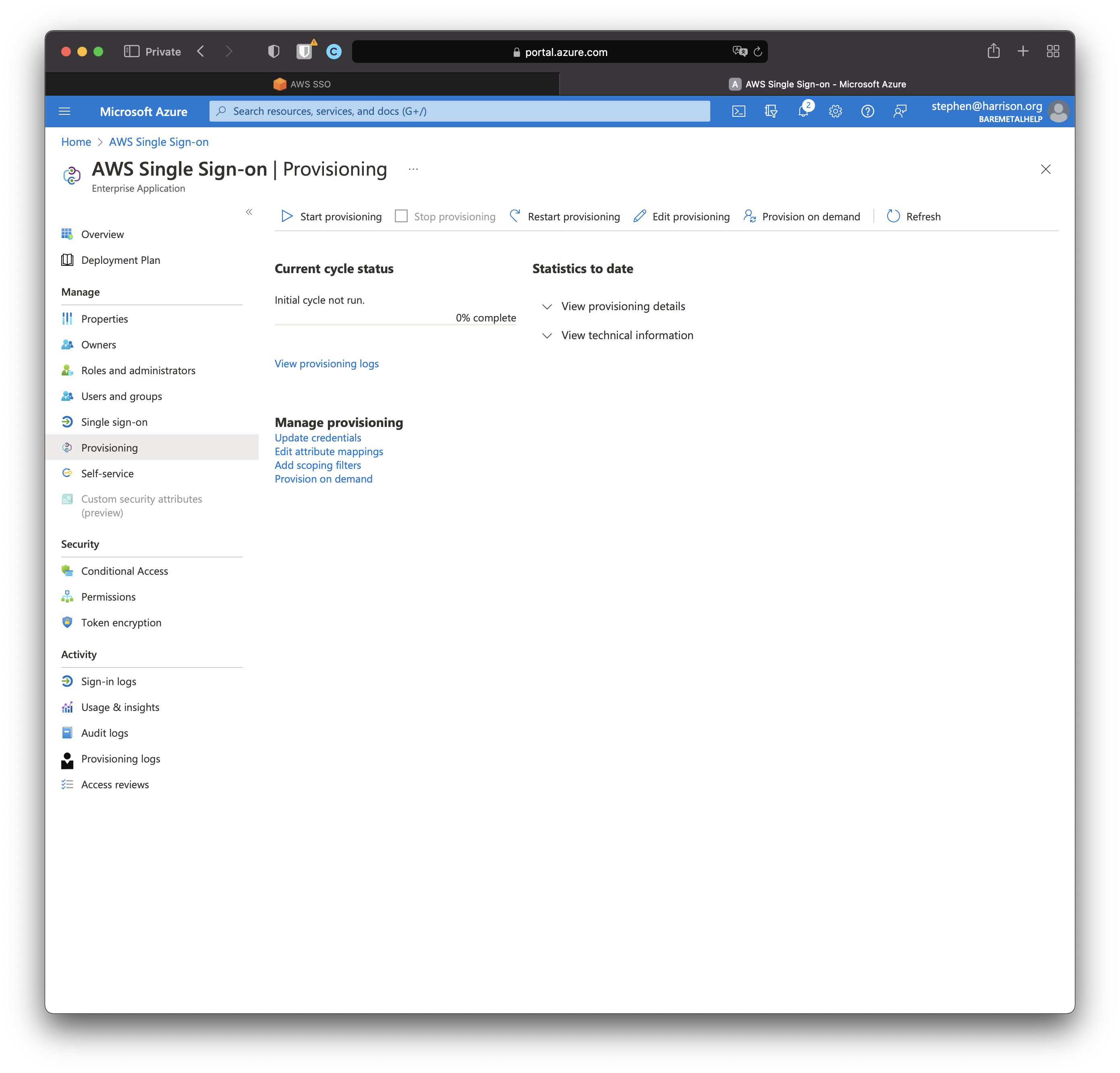
Click "Start provisioning".
Nothing will happen for a bit, so put the kettle on.
By default, synchronization runs every 40 minutes. It is not possible to change this delay. But it is possible to "Provision on demand" on a specific AD User. Although this will not create new SSO Groups, just assign existing ones.
For this step we're only interested in seeing all users and group being synchronized at once to AWS SSO.
We're so close we can taste it.

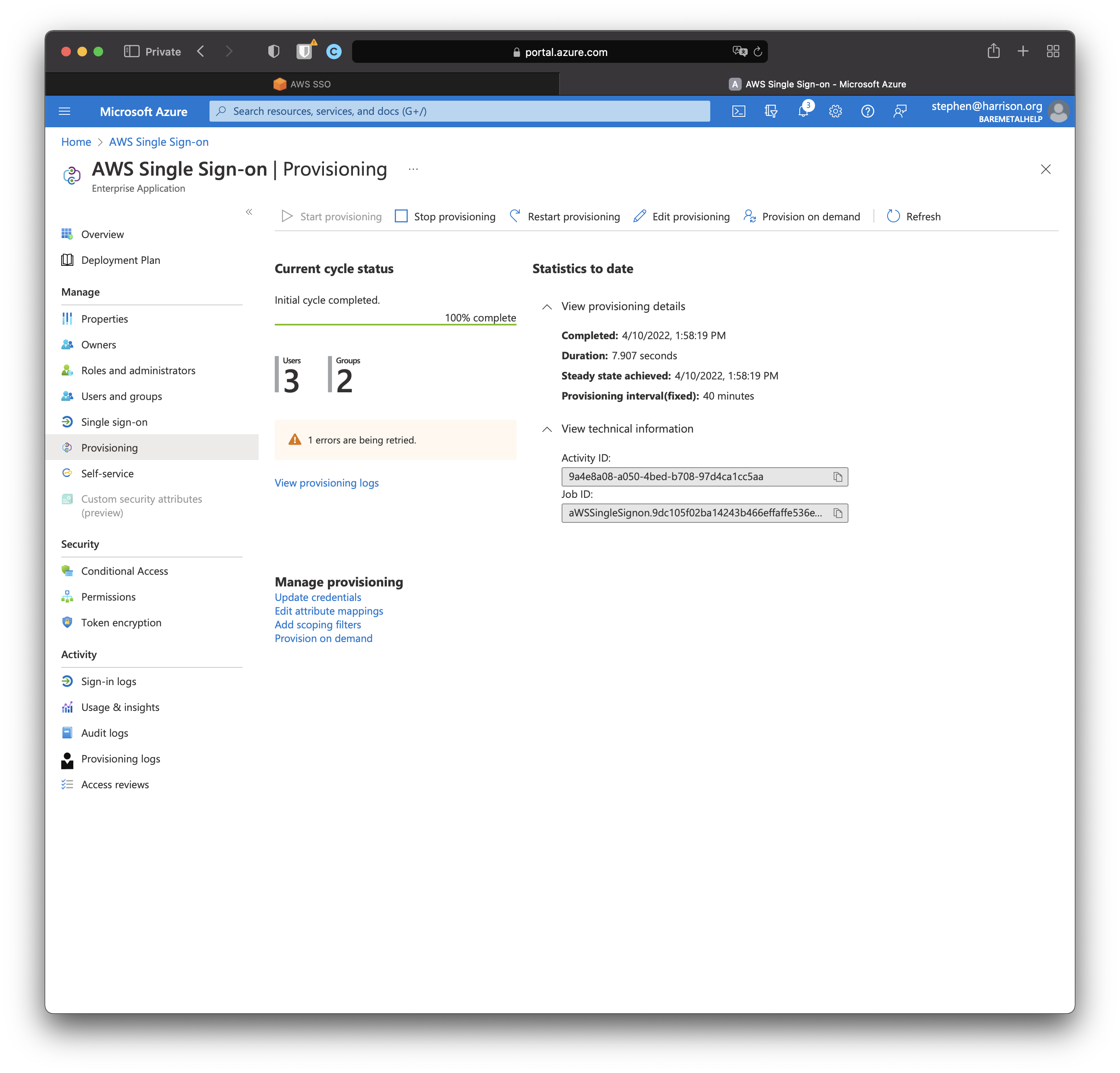
Oh look. An error. Let's show you how to debug and fix that.
First, let's head over to the AWS SSO Console to see what we can find out. Check Users and Groups.
Open AWS SSO console. Click "Users", then click "Groups".
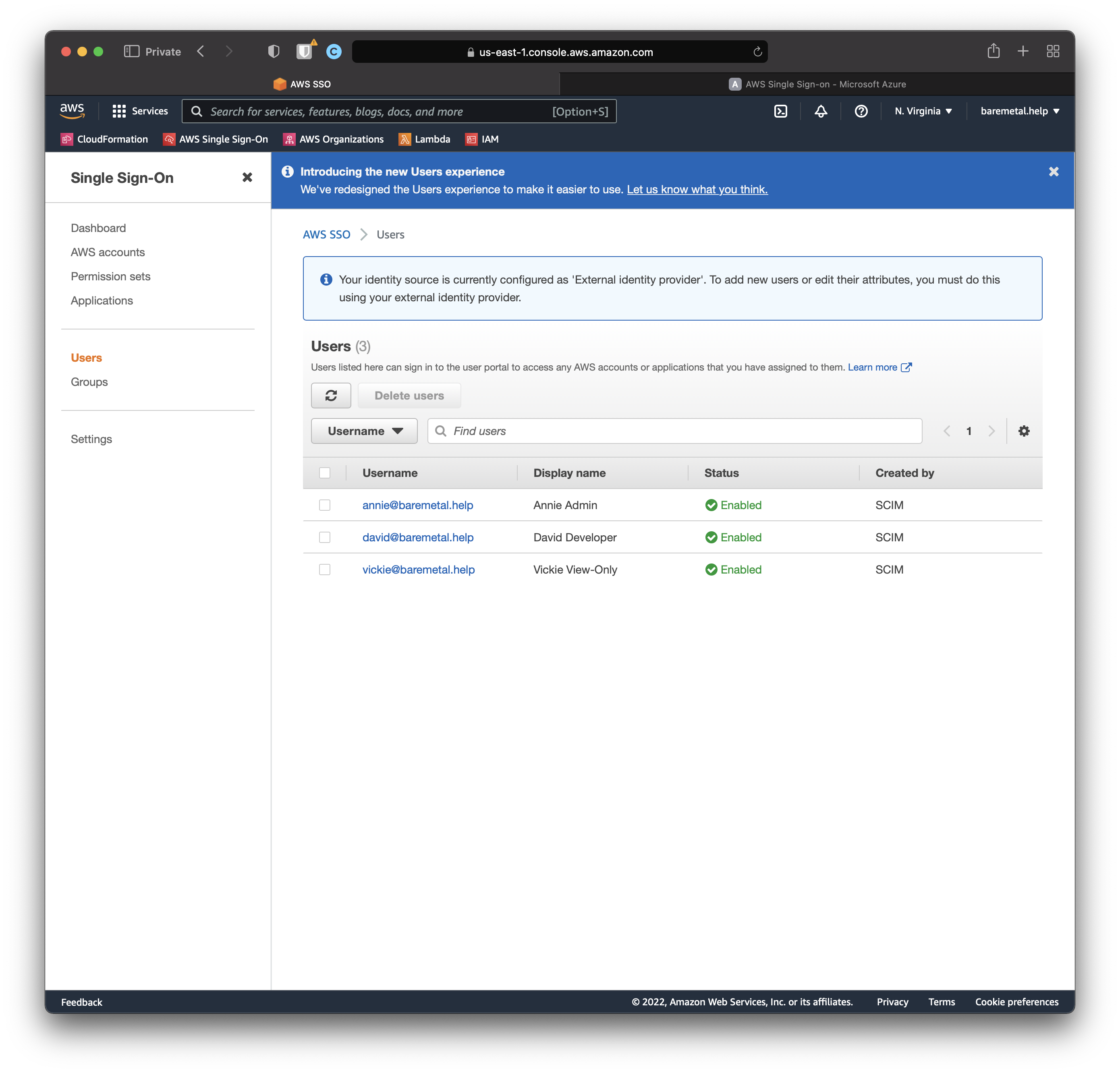
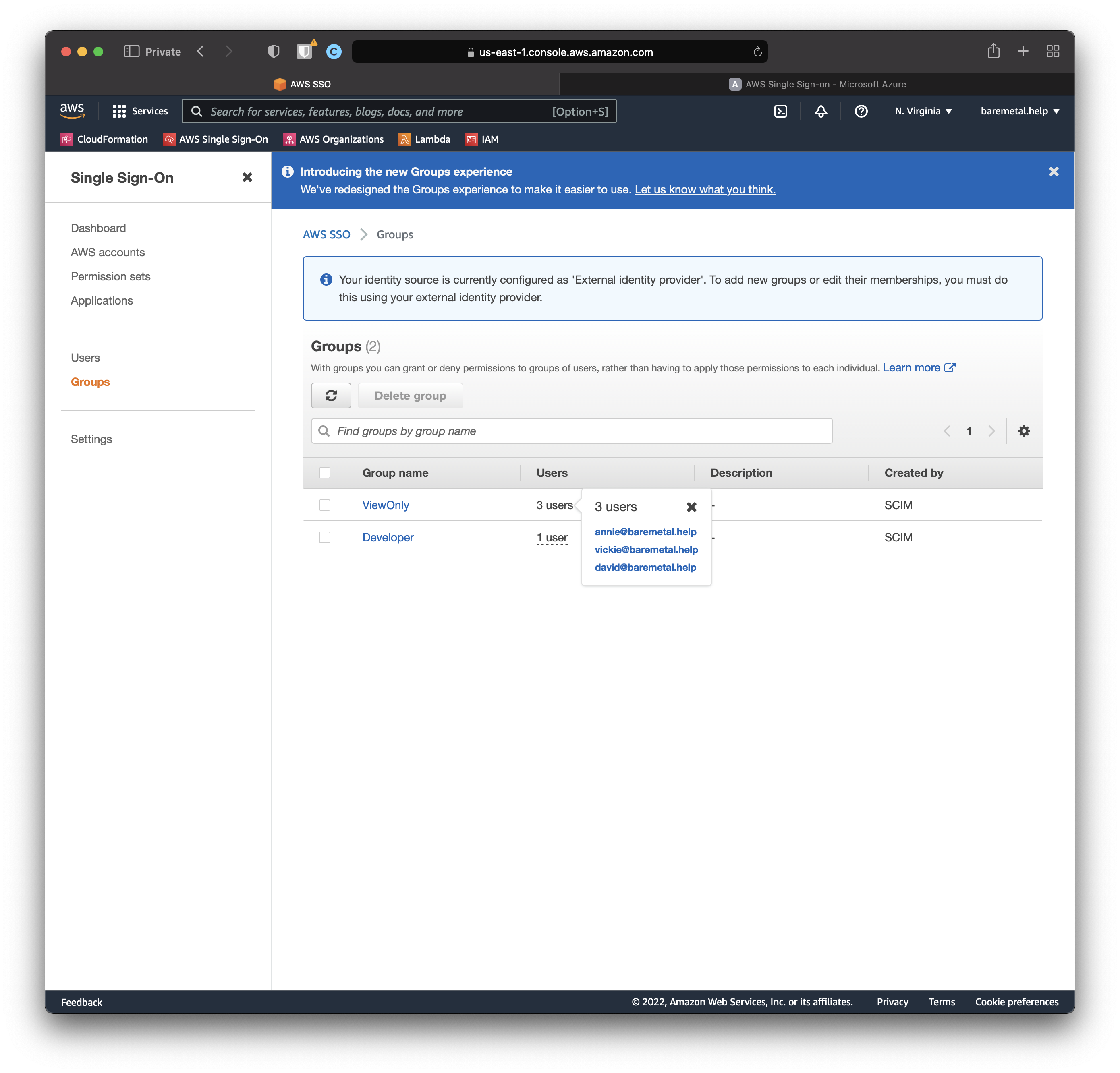
It looks like although Annie was synchronized correctly, the Administrator group did not.
Click "Provisioning logs" and find the failure.
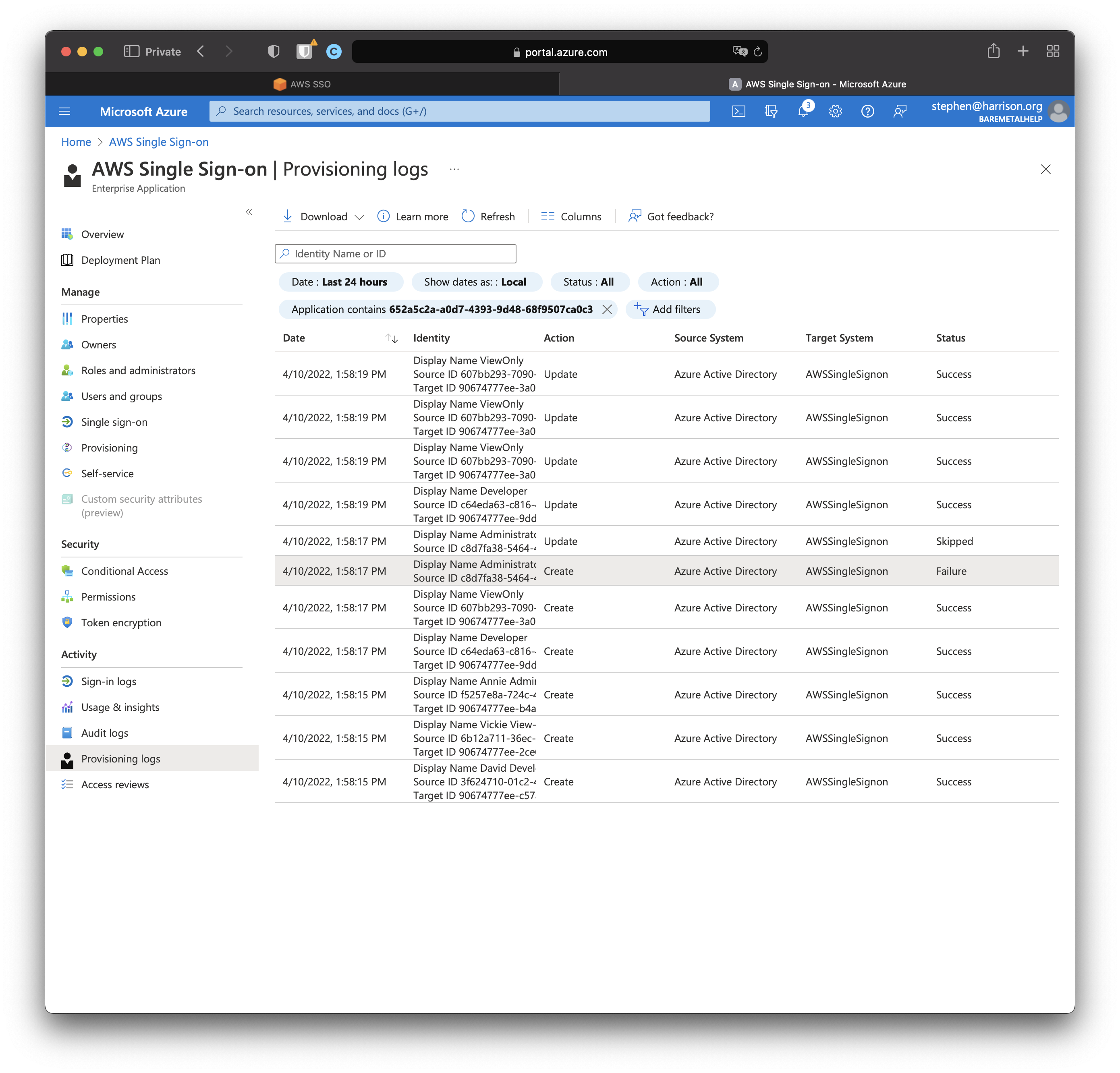
Click the failed entity.
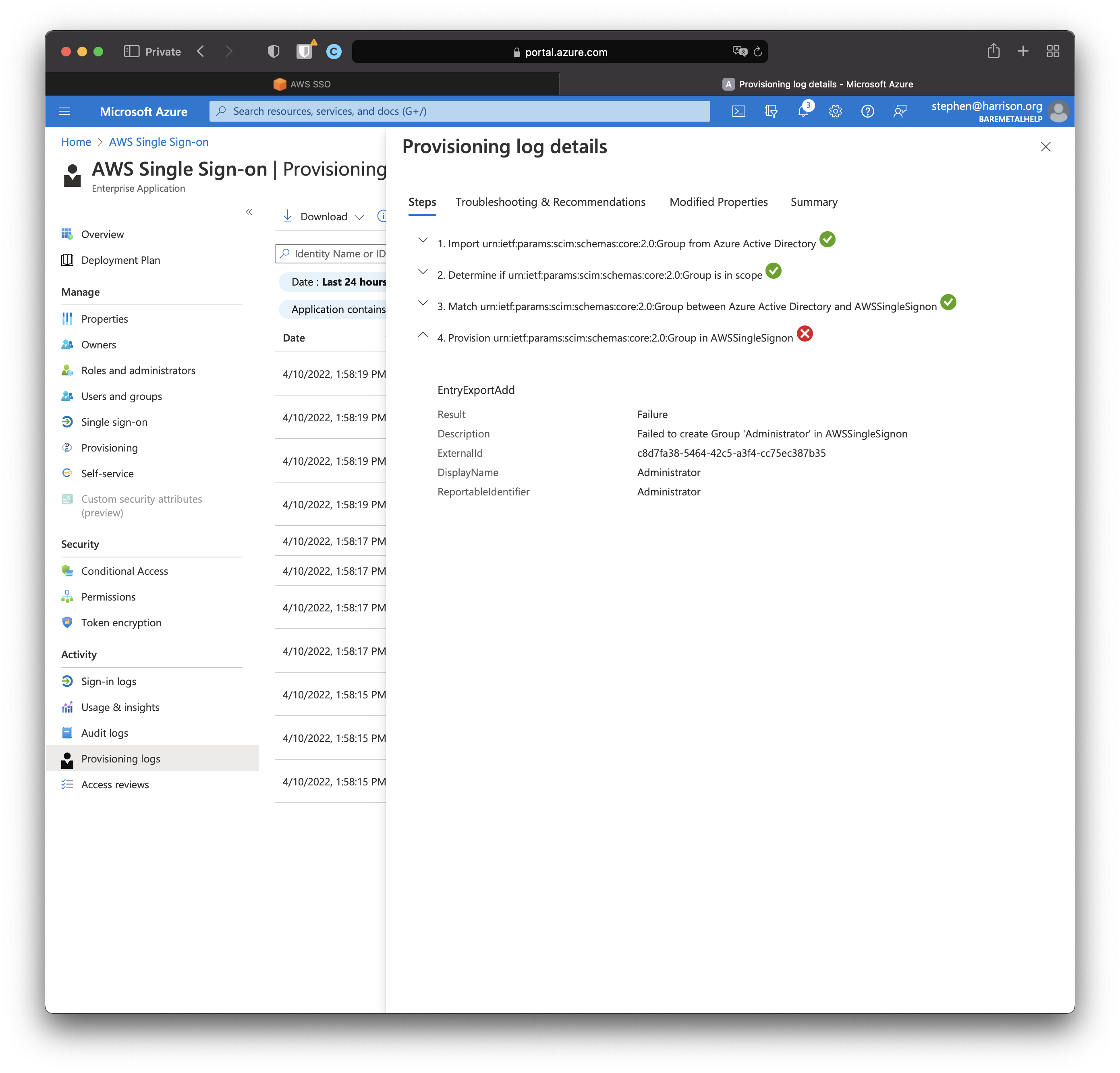
It's quite possible some group names are reserved, either in AD or AWS SSO. "Administrator" could be one of those. Let's add a new group "SRE" and see what happens.
Bingo.
State of Play
Tie it all together... TBD